
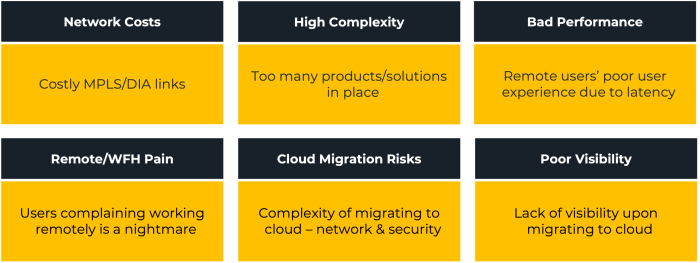
“After decades of focusing on network performance and features, future network innovation will target operational simplicity, automation, reliability and flexible business models.”

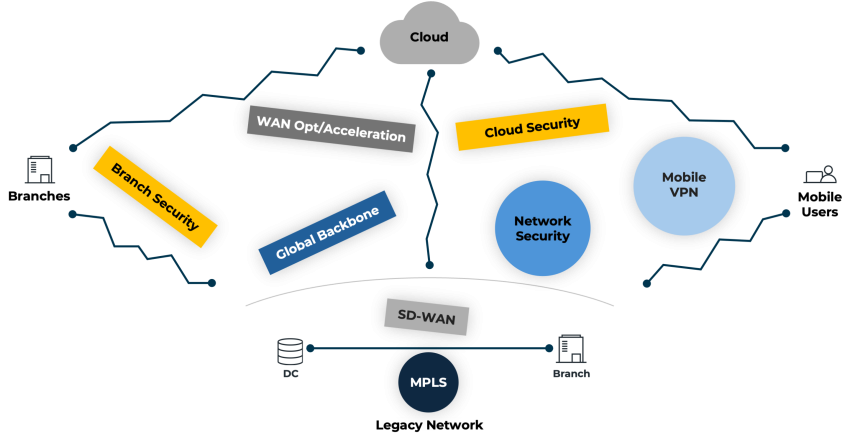
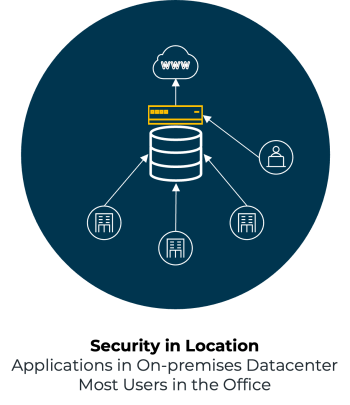
“Digital transformation and adoption of mobile, cloud and edge deployment models fundamentally change network traffic patterns, rendering existing network and security models obsolete.”

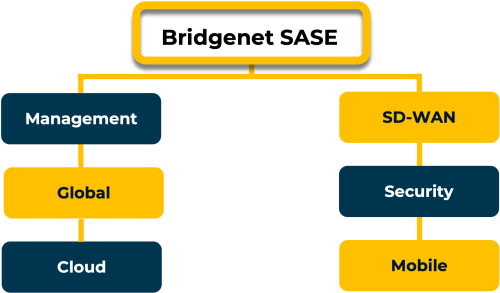
With Bridgenet’s Secure Access Service Edge (SASE) Service
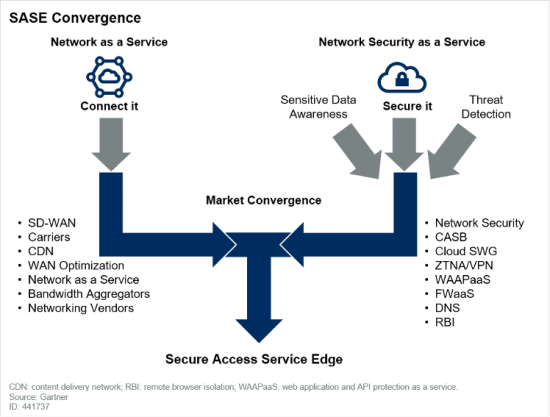
“Customer demands for simplicity, scalability, flexibility, low latency and pervasive security force convergence of the WAN edge and network security markets”.

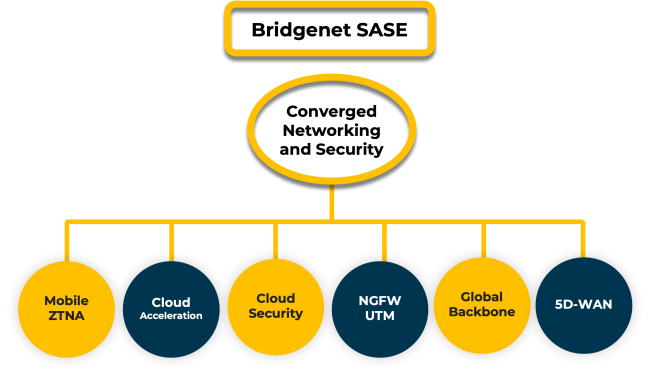
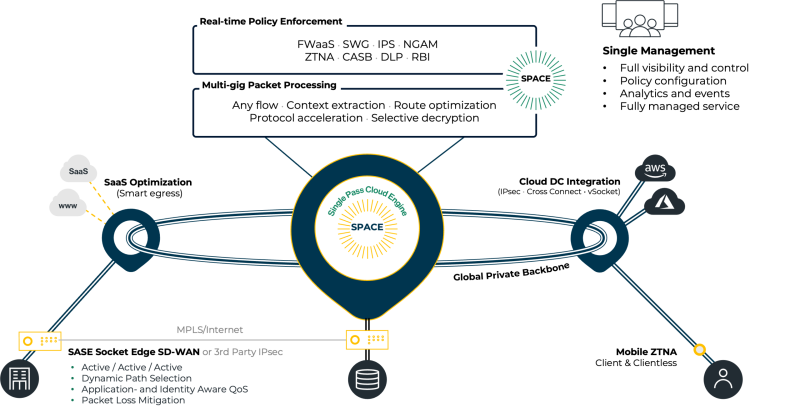
Bridgenet’s SASE service offers a unified software architecture, combining both network and security offerings.

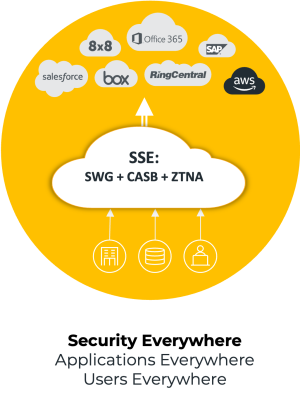
All Traffic, Same Security
One architecture for all edges
One policy engine and rule base
All traffic, all edges, all directions
With global private backbone
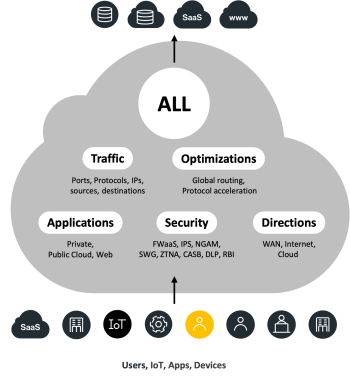
Security that follows the user
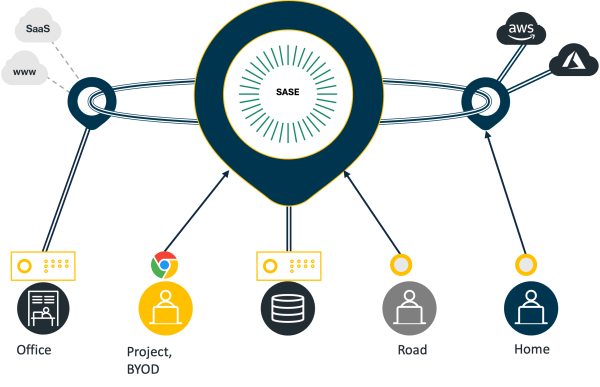
Consistent Policy for Users Everywhere
ZTNA: Trust but Verify
Securing all traffic from all edges
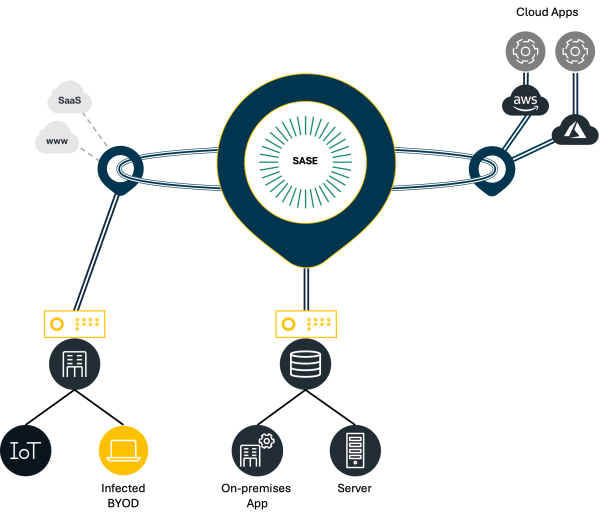
Edge to Edge Visibility
Edge to Edge Control
Securing all traffic from all edges
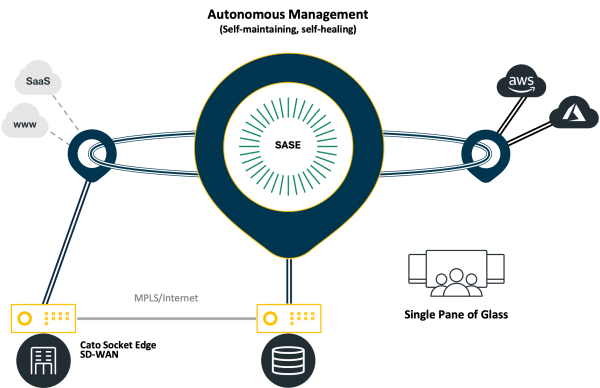
End-to-End Visibility and Control
Eliminate Solution Sprawl
Autonomous Management